Operational Technology Cybersecurity
- Home
- Products & Services
- Operational Technology Cybersecurity
Purpose-Built Protection, Backed by People Who Understand OT
At Logi-Tech, we know that protecting operational technology isn't the same as protecting traditional IT. Your industrial environments, legacy systems, and critical infrastructure need more than off-the-shelf security, they need a solution designed for the realities of OT.
As OT networks grow increasingly connected to IT systems, the attack surface expands, bringing greater risk to industrial control systems, legacy devices, and critical infrastructure. Traditional antivirus and EDR solutions fall short in these environments.
Logi-Tech is your local support team. We understand your industry, your systems, and the importance of uptime. Let's secure what matters most .
We've partnered with ARIA Cybersecurity to bring you a revolutionary AI-driven defence mechanism for OT, called ARIA Zero Trust PROTECT™
ARIA Cybersecurity has been providing its customers with peace of mind for more than 50 years, including some of the most critical organisations in the world such as the US Department of defence and other Western intelligence agencies.
AI-Driven Endpoint Protection for Operational Technology Environments
"Protect What Keeps You Running."
ARIA Zero Trust PROTECT (AZT PROTECT™) is a comprehensive AI driven defence system that protects all your OT endpoints from ALL cybersecurity threats – known and unknown.
This breakthrough patented solution represents a leap forward in the evolution of cybersecurity, surpassing anything available today. It protects your entire OT device infrastructure and critical IT applications no matter their location, safeguarding your revenue and reputation. It automatically blocks virtually all vulnerabilities from exploit at the application and OS level.
It does not matter if it's a ransomware attack, an unknown application vulnerability, a supplier with seemingly legitimate but compromised code updates, or a sophisticated threat that has never been seen before. You are always protected.
Unlike current cloud-based endpoint protection approaches, AZT PROTECT renders vulnerabilities irrelevant, and starts doing so straight out of the box. It keeps your OT environment up and running as well as ensuring compliance with evolving insurance and regulatory requirements.
It is time to get off of the treadmill of continuous security patching while remaining one step behind the attackers. It is time to get one step ahead by rendering all vulnerabilities irrelevant.
AZT PROTECT's AI-Directed patented approach
- Stops all attacks immediately as they try to execute
- Stops attacks Cloud based EDRs don't: Supply chain attacks, and Nation state backed attacks
- Understands known good applications, processes, etc… and blocks the rest
- Each endpoint is fully autonomous, stops the attacks then reports: No need for Cloud updates to block new attacks
- Makes application vulnerabilities and patching near irrelevant by blocking exploits
- No need for cybersecurity trained staff
- Deploys and fully protects in minutes
- Lightweight – can be rolled out on OT equipment with 20-year-old OS versions
- Can run fully air-gapped
Best Fit For:
- Legacy industrial environments
- Defence supply chain environments
- Energy & utilities
- Transportation systems
- Critical manufacturing & process control
- Government, water, and public infrastructure
Get Started
Protect your OT environment before attackers get in.
Contact Logi-Tech to book a demo or risk assessment today.
📞 Contact: Ben Kirk – bkirk@logitech.com.au
📞 Phone: 0498 588 344
Blogs about Operational Technology
Features and Benefits
- Provides complete protection against all forms of cyberattack, including unknown vulnerabilities and zero-day threats. Neutralizes threats in memory at runtime and on disk. Set it up one time and you are done. No daily tuning required.
- Safeguards all endpoints across the OT network, offering maximum protection with minimal computing power and no disruption to production operations.
- Works out-of-the-box and is up and running in minutes without the need for specialized cybersecurity expertise or training.
- Tailormade for a range of OT environments, including fully air-gapped setups, requiring no internet connectivity during operation.
- Can be deployed as a cost-effective outsourced service with round-the-clock monitoring via the US-based ARIA Security Operations Center (SOC).
Today's Current security framework can't stop unknown threats effectively
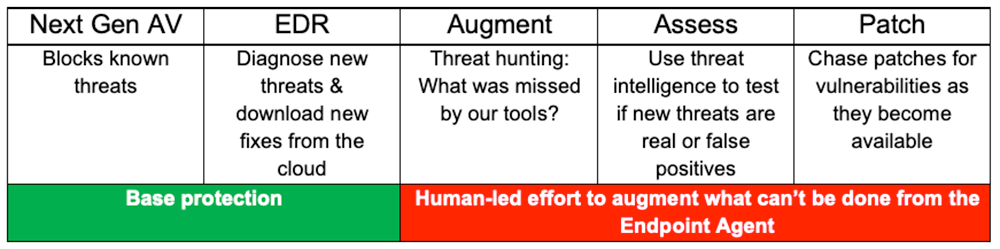
Today's best EDR solutions rely on outdated cloud-based techniques: discovering a new threat on a customer machine, analyzing the attack in the cloud, and then pushing out a solution. This approach captures unknown processes on your devices then sends them to unknown countries to examine your data. It can take months to come back with a solution to block exploits, which will deploy on your endpoints, despite being untested in your environment.
Advantages of AZT PROTECT
- Comprehensive Protection: It guards against all cybersecurity threats, including zero-day attacks, by understanding and allowing only known good applications and processes.
- Operational Efficiency: AZT PROTECT is autonomous, requires no cloud updates to block new attacks, and is lightweight enough to be deployed on legacy OT equipment.
- Future-Proof Security: By making application vulnerabilities and patching nearly irrelevant, AZT PROTECT offers a forward-looking approach to cybersecurity, keeping OT networks safe from the most advanced threats without the need for specialized cybersecurity staff.
This shift towards a more efficient, AI-driven security approach allows organizations to stay ahead of cyber threats, safeguarding their operational integrity and ensuring continuity.
AZT PROTECT solution architecture
- The AZT Trust Agent protects the OT network perimeter on all endpoint devices, spanning desktop, laptops, and embedded devices. It takes up minimal space on a device, consuming less than 2 percent of CPU even on legacy systems deployed decades ago. It does not require internet connectivity, making it suitable for fully air-gapped environments.
- The AZT Trust Center provides a unified view of all endpoints and site locations for control and monitoring. This includes policy and device management, application management, and alert monitoring.
Designed to protect the most sophisticated OT environments
AZT PROTECT addresses the unique challenges of the OT environment while effectively stopping all forms of attack. It is simple to deploy and operate, requiring no cybersecurity expertise. It works seamlessly without impacting critical application performance and is backward compatible with legacy systems.
AZT PROTECT recognizes the growing convergence of IT and OT, protecting all your critical application endpoints wherever they may reside. It provides comprehensive coverage across your entire organization, from legacy systems to manufacturing devices to critical IT backend applications.
AZT PROTECT supports all enterprises that rely on business-critical OT networks. This includes sectors such as pharmaceuticals, manufacturing, logistics, transportation, and energy and utilities.
Get Started
Protect your OT environment before attackers get in.
Contact Logi-Tech to book a demo or risk assessment today.
📞 Contact: Ben Kirk – bkirk@logitech.com.au
📞 Phone: 0498 588 344
Blogs about Operational Technology
Logi-TechOT powered by ARIA Zero Trust PROTECT (AZT)


